Small Businesses Make Big Targets
Reading Time: 3 minutesUpdated on Jan. 10, 2020
If you are running a business, spies are probably running along. Unseen, they are watching for the weaknesses to exploit. Read the article and learn how hackers rob businesses and how to protect yours.
There are two ways of gathering information about your competitors. One is by resorting to what’s in the open — analyzing their business associations, financial reports, public statements, market statistics, and so on. It is called competitive intelligence, and it’s legit. Another way is by going shady and embarking on what is called corporate espionage. It can be domestic and international. And like with most iffy practices, it’s bigger than one probably thinks.
In fact, international corporate espionage is so big, hacker attacks aimed at stealing intellectual property cost the US economy about $400 billion a year. And China is believed accountable for nearly 90% of those attacks, which is equivalent to $360 billion, or about two California annual budgets.
Chinese hackers steal more than twice the California budget in intellectual property annually. Click To TweetThis loss is cumulative of all types of businesses. Another interesting thing is that, because most data breaches that gain public attention concern big corporations, smaller businesses vastly underestimate the danger and often neglect deploying sufficient cybersecurity budgets.
Here are the grim statistics:
- 51% of SMBs do not allocate any budget on risk mitigation
- 38% regularly update their software
- 22% encrypt databases
- 75% of SMBs lack cyber liability insurance coverage (CLIC)
- 81% of SMBs that suffered a data breach didn’t have a system to detect it: if they did, it would have taken them an average of 14.5 days to inhibit a breach, as opposed to 145 days when reported by a third party
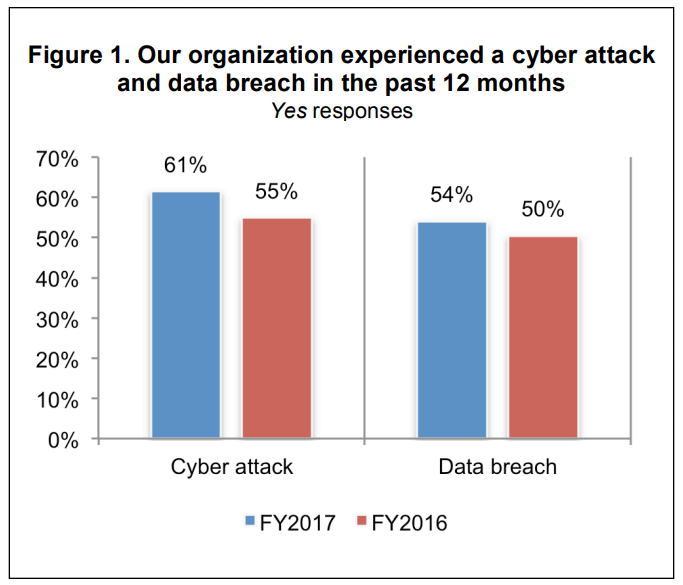 Source: 2017 State of Cybersecurity in SMBs, Keeper Report
Source: 2017 State of Cybersecurity in SMBs, Keeper Report
Among reasons small businesses give to this laid-back attitude is that they don’t believe they store anything of interest to hackers. Curious, for 68% of them reported storing customers’ email addresses, 64% — billing addresses, and 54% — phone numbers. All this data is sold great on black markets.
Hackers, like sharks, are always around sniffing for blood of careless businesses. If your company develops proprietary solutions and/or works with many customers, you make an attractive prey. If they feel the weakness, they’ll dart for you. Lack of protection makes SMBs an easy treat for cybercriminals. In fact, 43% of all cyber attacks are aimed at small and medium sized businesses. And 60% of those attacked cannot recover and go out of work within 6 months.
Hackers kill 60% of SMBs they attack. Click To TweetWhere does the threat come from?
Data breaches are usually performed using spear phishing, malware, and traffic interception. Hackers are lurking. Add employees’ negligence to it, and you get a ticking bomb ready to explode any moment. Most traffic interception attacks happen on open WiFi hotspots, when a traveling or remote employee logs into them for work purposes. Now, let’s consider the following.
An experiment was held by Avast in 2016. They set up bogus WiFi hotspots outside the National Republican Convention to see how many people would fall for them. As a result, 1200 attendees connected to these hotspots, 44.5% checked their emails, and 68.3% exposed their identities. If Avast people cared to, they could have gathered a lot of secrets that day.
And here is a follow up. Luke Bencie, Managing Director of Security Management International, says, “… one of the most dangerous locations anyone can use to check and send email is an international airport terminal and their hotel room. Complimentary WiFi networks are notorious for allowing operatives to intercept such activities. In many cases, host governments provide these networks specifically to create data-collection opportunities.”
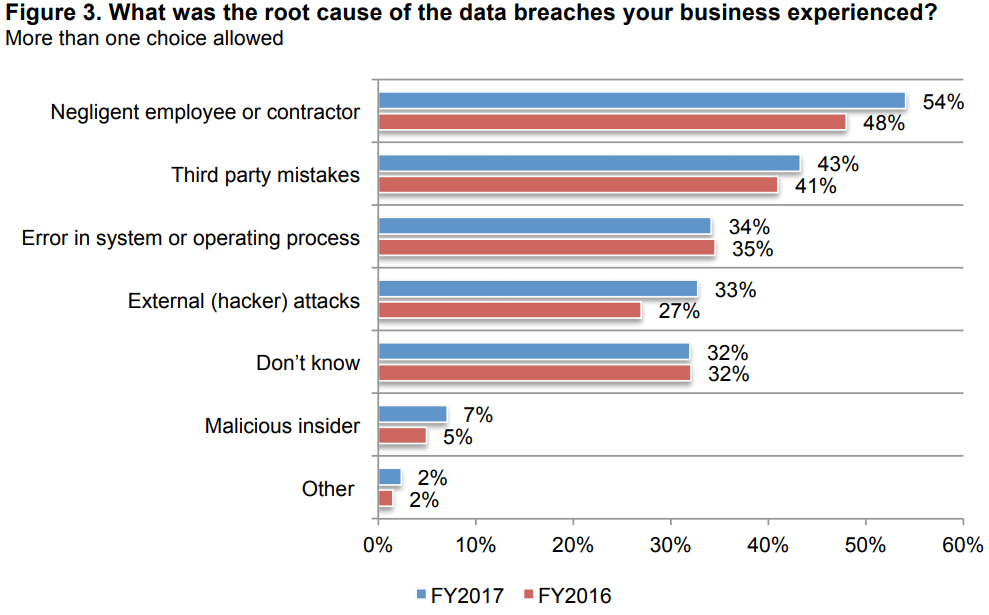 Source: 2017 State of Cybersecurity in SMBs, Keeper Report
Source: 2017 State of Cybersecurity in SMBs, Keeper Report
What we can gather is that people will use open hotspots no matter what, and that those are extremely dangerous. But neither work convenience nor its safety has to be compromised. If your company’s security culture includes using a reliable corporate VPN, such as VPN Unlimited Team, your employees can always safely connect to your business networks and resources from even the shadiest WiFi hotspots they can find, and thus be more accessible and free in their work. Business VPN app encrypts all their traffic, rendering it completely useless for those trying to bait out users’ secrets. Or if you need to encrypt only your office network, you can get a VPN for Routers. It’s only up to you, which solution to choose.

© GIPHY